Frequently Asked Questions about e-Contracting
The answers to these frequently asked questions may help you decide to upgrade from slow and cumbersome paper processes to e-Contracting.
By adding electronic signatures with digital signature software, your company can take advantage of the Internet's worldwide reach. The speed, efficiency and greater insight gained with an electronic contracting system are sure to delight management.
Check out our How-To Guides to learn how to use and configure eSignForms.
How to I get technical support or ask questions?
For eSignForms questions, we have a forum we recommend you check out first. Often you will find that your question has already been answered there:
- For any questions, visit us on our 'Yozons eSignForms Google Groups discussion board.
- To learn how to use or configure, check out the How-To Guides (User, System Administrator, Point & Click Programming).
To report a software bug that you'd like to track to resolution, use our 'openesignforms' GitHub Issues page.
For all other purposes, please visit our contact us page.
Are electronic signatures legal?
Yes. Electronic signatures were made legal throughout the United States when President Clinton signed the ESIGN Act of 2000. Similar legislation has been passed in many other countries.
Key features of legal electronic signatures include:
- Knowing who the parties are when they sign;
- Having those parties agree to use electronic signatures and show they are technically capable of signing electronically;
- Ensuring each party who signs receives a copy of the electronically signed documents (including the ability to re-verify those signatures electronically); and
- Ensuring that a forged or tampered electronic document can be detected.
What are the main laws and regulations that surround privacy and electronic records?
In the United States, there are laws regarding electronic records, record retention, privacy and electronic signatures. These include SEC 17a-3 and 17a-4, the Gramm-Leach-Bliley (GLB) privacy act, the Health Insurance Portability and Accountability Act (HIPAA), 21 CFR Part 11, Sarbanes-Oxley, the Government Paperwork Elimination Act (GPEA), the Uniform Electronic Transactions Act (UETA), and the Electronic Signatures in Global and National Commerce Act (E-SIGN). Yozons designs its solutions to help you comply with any and all of these laws and regulations.
Do you have a free version?
Yozons has never offered any of its products for free, and we're blessed with a continuously growing client list since 2001. Everyone knows that you get what you pay for. Most free things either bombard you with advertising, give you little real functionality until you "upgrade," or the vendor sells your personal and demographic information, along with those who electronically sign your contracts, to marketing companies, "partners" or "subsidiaries" that mine your data. For some small entities or for occasional personal use, that may be a fine trade-off, but no real business can rely on such low-end services.
Per our privacy policy, we no longer publish any information about new customers. This protects Yozons and all of our customers from hackers who exploit such information. Besides, don't be fooled by customer lists as most businesses will tout a Fortune 500 customer who bought $250 worth of services just once for a trial as if it were a long-term, high-value endorsement. Have you ever noticed how every company describes itself as being the "leader"? Only Yozons keeps its clients' information private -- technology and management you can trust.
We've been using paper forever. Why shouldn't I just continue with paper?
Paper is familiar, but paper is expensive to buy, to store and to dispose of in a way that's kind to the environment. Paper is hard to backup, requires lots of filing cabinet space, is expensive to store offsite and requires shredding when they are no longer needed. (How often do you scan your files for records that have passed their record retention dates?) Paper files are often misplaced, taken home or stored at an employee's desk, making them hard to find. Few people take the time to copy their documents, so theft, fires and disgruntled or forgetful employees can cause the loss of your valuable paper records. You may not even realize a document is missing until you look for it.
With Yozons, you no longer have to print your documents to dispatch them or get them signed. If you created a document electronically, why not keep it electronic? Electronic records are easy to backup, share, search for and store offsite. With auditing and tracking, you can be sure you know about every contract that's sent out, which is difficult in a paper world. Finally, when a record has met its retention requirements, it can automatically be deleted.
Why not just use faxes? Everybody's got a fax these days.
Updated 2015: Few people have faxes anymore!
Most businesses have fax machines, but few individuals do, and faxing is clearly in decline, despite the valiant efforts of e-faxing vendors who are attempting to bridge the chasm. The degraded legibility of faxed documents can make them impossible to read, especially if the recipient's fax smudges or is low on toner or if you need the fax signed and faxed back. Many people print a document just to fax it, which wastes paper and your money. If it's already electronic, keep it electronic.
Finally, faxes are typically sent to a common machine that is shared among an office, meaning that your correspondence can be read or mistakenly picked up by others. Besides, who really likes to create a cover page, punch in a phone number and wait 30 or more seconds for each page to go out, especially when the recipient's fax machine is busy or out of paper? If you need to send the fax to more than one party, the wasted time and phone charges add up quickly.
Overnight and second day delivery is pretty fast. Why not just use regular mail, FedEx or UPS?
For parcels, these are clearly the best way to move things across the world. But when your documents are created electronically, the costs of printing, addressing an envelope, paying postage and then waiting for pickup and delivery are simply much higher than using secure document delivery. While overnight may seem fast, with Yozons you can have someone sign a document or fill out your forms while you are talking with them on the phone, or you can complete a delivery in seconds even when the post office or UPS Store has closed for the day. Besides, would you rather pay a little to send your documents for signature in just 5 seconds, or pay $10 to $30 roundtrip to do the same thing using a courier in a 172,800 seconds (two days!)?
I don't think electronic signatures prove the identity of the signer as well as handwritten signatures.
This thinking has allowed a lot of fraud to take place over the years. Very few people have signature cards on hand to verify a handwritten signature, and fewer still are trained to detect forgeries. Most people's signatures vary slightly each time they sign so checking is complicated further, and many signatures are so stylized that they are impossible to read. With the advent of high resolution printers, scanners and copiers, it's very easy to make a perfect copy of even the most complex handwritten signature and include it on any document.
Most people are surprised to learn that banks and credit card companies rarely verify a handwritten signature precisely because it's so hard and expensive to do. It's easier and cheaper to wait for someone to complain about being defrauded than it is to check routinely.
With Yozons, electronic signatures cannot be copied and used on other documents. In the end, it is up to your business processes to weigh the risks and rewards on any transaction.
Aren't handwritten signatures more legal than electronic signatures?
Absolutely not. Various laws have endorsed electronic signatures for years now. Other laws require businesses to switch to electronic records that can be better protected and tracked. Aside from the problems of verifying a handwritten signature, multi-page documents typically have signatures at the end, so replacing earlier pages or marking up a change can complicate determining whether a given document is an original or not. With Yozons software, any such change to a document would easily be detected by a computer, even years later, so you can rest assured that what you sign can never be changed after the fact. Also, each time you sign a document, a receipt is sent to notify you that your signature was added. With complete tracking, it easy to find out all documents that you've signed, something that's impossible to do with paper records, especially if someone signs your name without your consent.
In practice, it is quite rare for a contract dispute to arise over whether a contract was signed or not. Mostly, disputes surround the meaning and interpretation of the contracts themselves and whether the parties lived up their respective obligations. Because it's so easy to forge handwritten signatures compared to electronic signatures, electronic signatures are more secure and reliable should a conflict arise.
A few people still feel that signing a paper record is more secure than doing so electronically. While it is important to select a hard-to-guess password that unlocks your electronic signature potential, a signed paper document (absent hand delivery and a notarized signature) suffers many problems that electronic signatures resolve.
The problems with paper-based signatures include:
- When documents are mailed or faxed, the intended recipient is rarely the only person who gains access to the document; co-workers, family members, neighbors and thieves can often come between you and the fax or envelope.
- Paper documents can be altered after they have been sent out. This includes replacing pages or simply marking up a change with your pen. If the word "not" is crossed out or inserted by hand, the entire meaning of a document can change. How often do you carefully re-read the signed paper documents to determine if anything has been changed, added or removed?
- It's impossible to tell when a handwritten signature was applied.
- Few people actually sign their name identically each time they sign. Fatigue, being hot or cold, and even the quality of the pen or the paper can affect how your handwritten signature appears.
- Faxes are often hard to read, with the quality being degraded because the source document is not clear or the original paper is colored, or if the recipient's fax paper or toner is of a low quality. And a photocopy or fax of a previously faxed document is often impossible to read.
- Many handwritten signatures cannot be read clearly because they are highly stylized. What name actually is scribbled on that piece of paper?
- Few people are expert enough to detect a forged signature, even when it's poorly done. Few have a signature on file that they can compare a signature against, and only handwriting experts stand a chance when it comes to high quality forgeries. Most banks and credit card companies never check signatures on checks or credit card slips because it is so expensive to do so, and they have signatures on file.
- With the advent of high resolution scanners and copiers, it is easy to produce new documents that look like the originals, but with unauthorized changes.
- With a scanned image of your handwritten signature, it is extremely easy to insert that image of your handwritten signature on any document.
- There's no tracking of documents that have been forged with your handwritten signature, so you often won't know others are signing with your name until a crisis arises and you learn that you've been victimized by identity theft.
With Yozons, electronic signatures give you greater control over your signature:
- Notifications to process documents secured in your web contracting service may be delivered right to a person's email address, making it far less likely that another party will intercept it.
- There's no need to re-read a signed document because any change, no matter how slight, will be automatically detected and the electronic signature will no longer be valid on an altered document. What you send and what you sign are always the originals, relieving you of this burden and risk.
- Accurate timestamps provide a true record of when a signature was applied.
- Electronic documents can be copied repeatedly and each copy is a legal original. There's no degradation in quality over time or when it's sent to others for review.
- Electronic signatures include clearly typed names, so you know who signed. Misuse of images of your handwritten signature don't matter because the image isn't the legal electronic signature, the underlying digital signature created through mathematics and encryption are what protect you.
- A computer verifies every digital signature, so there's no issue with verifying the validity of a signature.
- Every electronic signature is unique, based on your encryption keys, the contents of the document and a timestamp, so you can't copy an electronic signature and apply it to another document or even to the same document but at a later date.
- Lastly, it is extremely rare that a contract is disputed over whether a document was signed. Usually, the issue is over the meaning of terms, whether a contract has been altered, or whether a party didn't live up to the agreement. With electronic signatures, there's never a concern about altered contracts.
I'm used to seeing handwritten ("wet") signatures. Can't I just use an image of my signature and be done with it?
Absolutely not! Images of handwritten signatures make fraud even easier because it's so easy to copy an image and use it repeatedly on other forged documents. Electronic signatures look nothing like your handwritten signature. Fortunately, just as a computer creates an electronic signature under your control, it also verifies them for you. Therefore, never rely on an image of a signature to prove anything, especially since printing a document that contains an image of your signature will even look like you signed on paper.
While it may seem nice to have a visible "handwritten signature" appear in your documents, the truth is that such signatures are easily forged and copied. This is true for any lock, seal or stamp that may appear to provide protection. Visible queues simply cannot be trusted for electronically signed documents. Only trusted software can verify electronic signatures, and electronic signatures are never legally recognized when printed on paper. In a litigious world, security best practices dictate the use of digital signature-based electronic signatures.
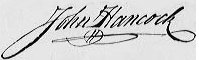 This image of John Hancock's signature was lifted from a copy of the U.S. Declaration of Independence. In the
paper world, seeing such a signature in ink is a reasonable way to believe that Mr. Hancock has
indeed signed, assuming that you can read it, you are a handwriting expert with a trusted signature sample on file,
and the person hasn't changed his signature over time.
This image of John Hancock's signature was lifted from a copy of the U.S. Declaration of Independence. In the
paper world, seeing such a signature in ink is a reasonable way to believe that Mr. Hancock has
indeed signed, assuming that you can read it, you are a handwriting expert with a trusted signature sample on file,
and the person hasn't changed his signature over time.Very few people are handwriting experts, and very few have signature files on hand to compare a handwritten signature against. The reality is that very few signatures, even those written on checks or credit card slips are ever verified because doing so is much harder and more time consuming than you might assume. With electronic signatures, you can verify a signature using software, so it's much easier to verify a signature and also ensure that the contents of what has been signed has not been changed after the fact.
Below is an example of a digital signature. Note that it looks nothing like a handwritten signature.
<SignatureValue>hEPnvrAAshuYb6lyK3vjx2nPkadxrksg6hRkjwPKFMxyqVAef5U3hoI1xmH1mYzCxl5h3WqhC07N x4HKvLeN8sgbgmAK4ioWPf3vKumKU0HlhQKZh9Q4WhaqOfmqaEBboO4nhjGgOuHlXvpNoQFgmlMg b9i6sb8cqV55Zwpfako9dczY7T/Juc9ac0Mr/q1L9aXwHY9HYSdvO6PqfFgwvwUPfo+hI2WjQeWO G0XSvkbqTm+2qjER8MrXYYOA5PBlrKkVbFHidIgLtsN8WhIrdDvlRrax9QfdBnGTlm+fLZ87sDUa UDScvFQ+wLcbeiOnJ+0MXlYiQrMwHWEDxLo4AgC6d6bHIC0/jKsNFqVORm+JAovTqFx/7ZNWJvUU dAAihdYh6CM8NXuAEA4y2EygCTer+tfVavkjtzc5pRAOGlYf9LUA7D3iHtvzJSblFcVXKL05kh71 hDWpyOHlmEQ0jb3Oksh4fp1Nv/0SWHIxSJaGgISZHowII6RR2vUB0otLq6jdg9DqOoTw1mxE6ipa heq0ptSq53pdf9/L8zqQC6XeLHxLknKqGpYUczB4E48bhyD7VVmDh+LedOYZaPNuUoCae2Pypg3d /Ct07RiuXRS0/FqYDn/xJtyciwExBElvBTHuL7+fMv3srSLw/+e54x9ayMzd0iofpdTxNnOnXjA=</SignatureValue>The above electronic signature shows a valid, unique XML digital signature. Unfortunately, this signature simply cannot be verified by a person. It requires that a computer running trusted software process the contents of the signed electronic document to recreate a hash (you can think of it as a unique fingerprint or the DNA of the document), then compare that computed hash value using the user's public encryption key and supplied digital signature to determine if everything is legitimate. If these computations match, then the signature is real and is associated with the given document. If not, then the signature is a forgery or the document is no longer the same as it was at the time the electronic signature was applied (it has been tampered with).
The human urge is to have a traditional looking handwritten signature appear within electronic documents that have been signed electronically. This urge must be resisted because it is an easy source of fraud. Why? Because it is easy to copy and paste an image of a signature, just as we copied John Hancock's signature above. That signature image can be cropped and resized to fit any document, and if you believe that seeing a traditional signature means it was signed, you will be easily tricked when you see the image.
Even worse, many people want to print electronically signed documents and have a signature image or seal appear on the paper copy. This is worse because once an electronically signed document is printed, the paper copy cannot be verified at all. Remember, people cannot verify electronic signatures, only computers can. Since it's easy to copy signature images and paste them into documents, printing them only makes those signatures appear more real because they are on paper. Modern scanners and photocopiers have made it nearly impossible to determine original handwritten signatures from copies. Some criminals even copy currency using these tools, which shows how easy it is to trick people with paper copies.
The lessons to take away with you are:
- Electronic signatures do not look like handwritten signatures; if they did, it would be easy to trick us into believing they are real because we are used to seeing them that way on paper
- Only electronic originals are legally binding because they can be checked using our trusted software to determine if they are authentic or not
- All computer files can be tampered with or simply recreated with new contents using the same file name
- Creating printed paper copies of electronically signed documents may be useful for storing in folders or to ease sharing with certain parties, but don't look for visual cues in the paper copies to determine if they are real or not (all visual cues can easily be forged on paper or electronically)
- Email is inherently insecure and unreliable and for this reasons Yozons remains web-based rather than using email itself.
Remember, some people are tricked into clicking links in forged emails (aka "phishing") purporting to be from PayPal, Amazon.com, Citibank, Microsoft, etc. These victims unwittingly provide their financial information to criminals who are operating web sites that look just like the real web sites because it's easy to copy logos, seals and other images that are electronic. Other people are tricked into installing viruses because they believe an email that appears to be from Microsoft or "a friend's email address" is valid just because a criminal has sent the fraudulent email using the other party's actual email address. These scams rely on the fact that people tend to trust official looking messages. In the electronic world, it's easy to fake how things look. Never trust the contents of an email sent to you.
I don't want my electronic signature "floating around the Internet" where someone can steal it.
Because electronic signatures are unique for every document you sign, nobody can copy an electronic signature and use it elsewhere. With our technology, the timestamp and IP address of the computer used are recorded, so even if you were to sign the same document repeatedly, the electronic signature would never be the same.
Why don't you use Adobe PDF files?
Adobe PDF was a fine read-only technology in its time, but it pre-dates the Web and just isn't suitable for online business today.
PDFs are not natively rendered in web browsers, so you need a proprietary plug-in just to view them, and then you can't interact with the document such as filling out a form or resizing it to fit varying computer window sizes. PDFs rendered inside a browser are clunky and confusing with their own buttons and controls. You cannot take advantage of the accessibility options built into modern browsers that support font legibility or screen readers, and of course they don't work well with the myriad new HTML-capable devices being connected to the Web, such as Apple's iPhone and iPad, Blackberry, or the various Google/Android smart phones. Furthermore, PDF files are significantly bigger than standards-compliant HTML files, wasting bandwidth and your time to upload and download them, not to mention the disk space consumed to store them.
And Adobe Reader has been known to have serious security flaws exploited by malicious PDFs that only compound the trouble of this antiquated technology, including virus-laden PDFs that look like they were sent via major, branded e-sign vendors. In fact, CNN reported Adobe has an especially abysmal security record in just about all of their technologies as well as their corporate record keeping.
NOTE: eSignForms allows documents to be exported in digitally signed PDF format to support legacy systems. Naturally, this PDF exporting makes no use of Adobe products to keep them free of viruses and other vulnerabilities.
Why shouldn't I just use a PKI (public key infrastructure) solution?
PKI has been around for a long time, but it has not taken off except in a few high security niches. The reason is that PKIs are complex, very expensive and suffer interoperability issues. The costs and pains of creating, distributing and keeping digital certificates secure on thousands of computers has been too high to make it cost effective except in small, closed networks. In a PKI, it is important to train all users how to keep their certificates secure (even when they upgrade their computers, have them serviced, replace a hard drive or when a virus strikes), install special software on every computer, and then exchange the public keys of all parties involved. Needless to say, PKIs simply have failed to scale outside of specialty networks.
Our technologies use the same digital signature technology behind a PKI, but they have removed the need to annually distribute certificates (there are none!), exchange keys (they are fully managed by the secure server), install special software or worry about keeping all users' computers secure.
PKI versus EBIA (Email-based identification and authentication)
Yozons Technology has streamlined PKI and created a better way to do business, taking its best points and transforming them into a far easier to use, secure system that doesn't require complex software, expensive digital certificates, hard to manage keys. You use the documents you already use as well as the email addresses you and everyone else already have. That's the key to our success (and our patents): significant cost savings, yet easily adoptable by you and all the many parties you need to communicate with.
Mr. Garfinkel, of the Massachusetts Institute of Technology (MIT) and author of Database Nation: the Death of Privacy in the 21st Century, wrote an interesting article* in the IEEE Security & Privacy journal. He explains that "email-based identification and authentication (EBIA) is a reasonable approach for many current commercial and government applications. EBIA provides a better match to the usability, privacy, autonomy, resiliency, and real-world business requirements than PKI [public key infrastructure] technology."
He points out that "even sensitive applications that let us enter into binding business agreements worth thousands of dollars and electronically transfer money between bank accounts, use EBIA."
To get EBIA right, it is important to determine that a given party can receive email at a given email address. It is quite hard to intercept someone's email (except for the system administrators at the person's ISP or IT shop who control the email or domain name servers). It is extremely easy to send email using anybody's email address.
In addition to using a user's de facto electronic id, the email address, we also send out email notifications as a means to allow him or her to self-audit or detect misuse of the account. For example, if you change your password or forgotten password question and answer, or get your password wrong multiple times in a row, an email is sent. These can help you detect misuse of your account as well as keep you informed about activity pending in your web account. If you forget your password, instead of sending you your old password (we simply cannot because we don't store your password anywhere) or even emailing you a new temporary password, we instead send an email to your address and require that you click on a unique link in order to continue.
When done right, these added precautions can mean the difference between EBIA working really well for you or discovering that EBIA is providing no security whatsoever. Yozons does it right, and that's why experts consider EBIA to be a workable solution that's better suited for business than even PKI and its digital certificates.
"Despite a tremendous push from management, security professionals, consultants, and vendors, the market and the general public have been slow to adopt PKI," Garfinkel wrote. For PKI to have failed to gain widespread adoption after so many years (the technology dates back at least to the early 1980s), the shortcomings must be real.
Garfinkel says explanations for PKI's failure include usability and cost, as well as the fact that "some experts insist that the claims made for PKI are unjustified, because computer viruses and other kinds of malicious software can compromise private keys or make people think that they are signing one message when in fact they are signing another." Nevermind the fact that most PCs are not kept in secure rooms, laptops are lost or stolen daily, people don't logoff when they step away from their computers (even if just for a brief moment), people don't back up their encryption keys and trusted digital certificates, and when people upgrade their computers they don't know how to transfer those encryption keys and digital certificates to the new computer while ensuring that the same data are securely wiped clean from the old machines.
PKI has touted non-repudiation as its major benefit, but reality has shown that people can tamper with and forge just about anything, including currency with its sophisticated paper, fibers, ink and printing processes. As Garfinkel notes, "Unscrupulous people can forge passports, steal SSNs and private keys, and tamper with biometric databases." PKI gives an illusion of perfect security, but "software flaws, stolen keys, or improperly granted certificates" have proven that's not the case.
While Yozons knows of several Fortune 500 companies that have scrapped millions of dollars "worth" of PKI digital certificates in favor of our technologies, Garfinkel also disclosed that even for the United States military, which has deployed four million client-side certificates, "many mission-critical Web sites -- especially those used in combat situations -- rely on user name-password authentication" precisely because digital certificates are not flexible enough to meet real-world needs. "While many organizations continue to invest in PKI, another technique for identifying and authenticating Internet users is rapidly emerging in the marketplace." That's EBIA.
While using email may seem insecure because it is sometimes transferred in the clear and "key employees at many businesses and Internet service providers (ISPs) can browse or perform keyword searches on users' mailboxes," EBIA is used widely, implying that the security risks are reasonably attractive to banks, the military and many other businesses. "EBIA has been successful because it combines ease of use with a limited challenge-response system that is not trivial to defeat."
Garfinkel continues, "A key advantage of EBIA over PKI is that PKI requires specialty software and a mutually trusted CA [certificate authority]. EBIA, on the other hand, can work with any email client (or even with Web-based email), using email addresses available from hundreds of thousands of different email-granting organizations (ISPs, companies, schools, government organizations, and so on)."
* All of the above quoted material is from the following article: "Email-Based Identification and Authentication: An Alternative to PKI?" by Simson L. Garfinkel, IEEE Security & Privacy, November/December 2003, pp. 20-26.
Will Yozons support the European Union's (EU) July 2016 updated Advanced Electronic Signatures Directive using eIDAS?
No. Yozons continues to believe in its patented solution that avoids the cost, complexity and lack of practical security sold as "advanced" by old school socialists who believe they can somehow make PKI work if they just beat its citizens into submission. Humans simply are not good at security, and their devices are even less secure. Of course, vendors that do support eIDAS include DocuSign and eSignLive, among many others in the EU. Unfortunately, such bloated, unproven "international standards" created by committee without practical experience have dominated history while failing miserably in industry: OSI Stack over TCP/IP, X.400 over SMTP, X.500 over DNS, SGML over HTML, ASN.1 over XML or JSON... There is a reason why e-signatures have been massively adopted in the USA compared to the EU.
What about PGP (Pretty Good Privacy) or other desktop encryption solutions?
PGP, created by Phil Zimmermann in 1991, is excellent software (as its the open source GNU Privacy Guard: GPG), but it requires that all parties purchase and install supported software, generate their encryption keys, and then exchange those keys in a secure way. If you forget the password that protects your keys, you will forever lock yourself out from your own documents and data!
PGP supports digital signatures that ensure the validity of a message or a file, but does not easily support multiple, legal electronic signatures to be applied, nor does it allow you to send a document and request the other party to sign your document.
Lastly, desktop encryption means that employees can surreptitiously send out confidential business information without your consent or ability to detect it. This can expose your business to various liabilities if the encrypted data includes your trade secrets, employee records, financial information, pornography or threats. Furthermore, encrypted messages cannot be scanned for viruses, audited or archived without the keys, and if the employee loses, forgets or otherwise decides not to provide those keys, your valuable data cannot be recovered.
What about S/MIME that's built into my Microsoft Outlook?
S/MIME, an international standard dating back to June 1999, is based on PKI so it suffers the same problems and high costs. Like PGP, it provides authentication, message integrity and non-repudiation using digital signatures and privacy and data security via encryption. Despite being available for many years in the leading email clients, it's adoption simply has failed to take off because of all the PKI headaches.
What's the difference between a digital signature and an electronic signature?
In a nutshell, most reliable electronic signatures are based on digital signature technology. Digital signatures are created by hashing data to produce a large number that uniquely identifies the contents (something like a DNA test for data) in such a manner that any change would no longer produce the same number. That number is then encrypted with your keys to prove that it belongs to you. Electronic signatures are a legal standard that may use digital signature technology, but they also require consumer disclosures, consent to use them, proof the user knew the signature was being applied on their behalf, and the assurance that each party is allowed to have an independent copy to prove exactly what and when it was signed.
We have more information on electronic signatures and digital signatures for those brave enough to wade into those waters!
Can I print an electronically signed document?
You can print the signed document and information that surrounds the electronic signature, but a printed version is not legally binding. Only the electronic document and electronic signatures together comprise the legally binding original. What is interesting, though, is that because electronic documents and signatures can easily be copied, backed up, archived, etc., all copies that are electronic are considered to be legally recognized originals provided the signatures can be re-verified.
For your legal protection, you should keep the electronic document and electronic signatures in order to be able to re-validate the signatures in the future because it's so easy to spoof, forge or tamper with anything that's printed on paper or stored in non-digitally signed electronic formats.
Even a Adobe PDF or other electronic file that simply contains images of or information about the electronic signatures is not legally binding without the electronic signature information in a form that you can use to re-verify the signatures. It is very easy to create PDF files and images that appear to be electronically signed, so never rely on appearances and instead rely on being able to re-validate the signatures using software.
Furthermore, you cannot combine electronic signatures with handwritten signatures precisely because the handwritten signature will be on paper and there is no way to verify the electronic signature information that appears on paper.
Why should I choose Yozons?
Yozons is privileged in that we can focus our energy on our patented, market leading, secure business process and electronic contracting technologies. Yozons, Inc. was founded in 2000, has been profitable since 2002, and has a high caliber client list that spans the Fortune 500 through small businesses.
We treat our customers, employees and partners the way we like to be treated, and this simple, yet rare, policy has served us well. Our technology is proven, secure, fast, inexpensive, reliable, scalable and doesn't require client software, plug-ins, special email clients, PKIs or any other obstacle to making your processes a success.
Please read more details that make Yozons special on our About Us page.
Does Yozons act as a disinterested, trusted third-party like a notary with respect to our e-contracts?
No, Yozons is a technology provider. Unlike our competitors, each customer's data and user accounts are stored in its own database and are not mixed in with data and users from other customers like those of our competition. We and our customers trust our software because it's available to anybody and thus shows Yozons has nothing to hide and uses industry standard technologies to provide a powerful, reliable, easy-to-use system that can't just disappear on the whim of an investor, acquirer or the like.
Yozons has no interest in your private documents and the parties you do business with, but you can trust that Yozons will help with any legal questions regarding our software that might arise from of a dispute.
Yozons operates numerous properties that our customers use for our shared hosted systems, and many of our customers run our software on their own private web servers that we manage or on their own servers in their data centers. We do not consider any of those sites as being part of our web properties because they do not use our domain names.
The list is ever changing, but here are the various web properties Yozons operates now on behalf of our shared hosting customers: eSignForms™, eSign-Contracts™ and eSign-HR™.
Why does my business/industry need to provide more detailed identity information to use the Yozons services?
Certain industries receive lots of complaints from end users who misdirect their inquiries to Yozons because they are not able to reach or get satisfactory customer service from those in these industries. Often such industries appear to mislead unsophisticated users into signing contracts they do not understand, make terminating a contract more onerous than entering into the contract, bill high rates without delivering quality products or services, do not return customer inquiries, or repeatedly do not handle complaints to their customer's satisfaction.
Yozons knows that many in these industries do provide value when done professionally and ethically, and the expectation is that those who purchase our services fall into this category.
For such industries -- including, but not limited to, coaching, debt relief and offers to sell or train for home-based businesses -- Yozons requires additional information to activate an account, including the company's federal tax id, state registration and a contact phone number that will be answered or receive a call-back within 24 hours.
Why did Yozons terminate or not renew my service subscription?
If Yozons receives more complaints than it is comfortable handling, we may choose to terminate service immediately (with a refund for any unused term) or simply not allow the service to be renewed once the current term expires.
Yozons' terms of service demand only legal and ethical usage, and numerous complaints misdirected to us indicate illegal or unethical usage. To avoid this, please provide quality service to your customers so that they do not contact us for problem resolution or refunds.